title: Solver Atlas Manuals
Solver Atlas Manuals
Solver Gateway creation:
apiVersion: networking.istio.io/v1alpha3
kind: Gateway
metadata:
name: solver-gateway
namespace: "default"
spec:
selector:
istio: ingressgateway # use istio default ingress gateway
servers:
- port:
number: 80
name: http
protocol: HTTP
hosts:
- "*.thingsolver.com"
tls:
httpsRedirect: true
- port:
number: 443
name: https
protocol: HTTPS
tls:
mode: SIMPLE
credentialName: solver-tls # must be the same as secret
hosts:
- "*.thingsolver.com"
Keycloak IDP configuration and deployment:
Keycloak values file
extraEnv: |
- name: KEYCLOAK_USER
value: someUsername
- name: KEYCLOAK_PASSWORD
value: aSecurePassword
- name: PROXY_ADDRESS_FORWARDING
value: "true"
- name: DB_VENDOR
value: postgres
helm repo add codecentric https://codecentric.github.io/helm-charts
helm upgrade --install keycloak codecentric/keycloak -f keycloak-values.yml #--version 17.0.1
Keycloak user setup:
Keycloak integration with LDAP:
Deployment of services:
An exemplary service
---
apiVersion: "apps/v1"
kind: "StatefulSet"
metadata:
name: "solver-foundation-meta-service"
namespace: "staging"
labels:
app: "solver-foundation-meta-service"
version: "v1"
solvertag: thingsolver
spec:
replicas: 1
selector:
matchLabels:
app: "solver-foundation-meta-service"
serviceName: "solver-foundation-meta-service"
template:
metadata:
labels:
app: "solver-foundation-meta-service"
version: "v1"
solvertag: thingsolver
spec:
terminationGracePeriodSeconds: 10
containers:
- name: "solver-foundation-meta-service"
image: "thingsolver/solver-foundation-meta-api:v3.1.8"
imagePullPolicy: Always
ports:
- containerPort: 8080
name: meta
command: ["/bin/sh"]
args: ["./run_server.sh"]
resources:
requests:
cpu: "100m"
volumeMounts:
- name: pv-claim-solver-meta-api
mountPath: /db
imagePullSecrets:
- name: regcred
volumeClaimTemplates:
- metadata:
name: pv-claim-solver-meta-api
spec:
accessModes: [ "ReadWriteOnce" ]
resources:
requests:
storage: 2Gi
---
apiVersion: "v1"
kind: "Service"
metadata:
name: "solver-foundation-meta-service"
namespace: "staging"
labels:
app: "solver-foundation-meta-service"
version: v1
spec:
ports:
- name: http-solver-foundation-meta-service
port: 8080
targetPort: 8080
selector:
app: "solver-foundation-meta-service"
version: "v1"
type: "ClusterIP"
---
apiVersion: networking.istio.io/v1beta1
kind: DestinationRule
metadata:
name: solver-foundation-meta-service
namespace: "staging"
spec:
host: solver-foundation-meta-service
subsets:
- name: v1
labels:
version: v1
trafficPolicy:
tls:
mode: ISTIO_MUTUAL
---
apiVersion: networking.istio.io/v1beta1
kind: VirtualService
metadata:
name: solver-foundation-meta-service
namespace: "staging"
spec:
hosts:
- "staging.thingsolver.com"
gateways:
- default/solver-gateway
http:
- match:
- uri:
prefix: /api/v2/foundation/meta
rewrite:
uri: "/foundation/meta"
route:
- destination:
port:
number: 8080
host: solver-foundation-meta-service
subset: v1
corsPolicy:
allowOrigins:
- exact: "*"
allowCredentials: true
allowMethods:
- GET
- OPTIONS
- POST
- PUT
- DELETE
allowHeaders:
- Authorization
- Content-Type
- match:
- uri:
prefix: /api/latest/foundation/meta
rewrite:
uri: "/foundation/meta"
route:
- destination:
port:
number: 8080
host: solver-foundation-meta-service
subset: v1
corsPolicy:
allowOrigins:
- exact: "*"
allowCredentials: true
allowMethods:
- GET
- OPTIONS
- POST
- PUT
- DELETE
allowHeaders:
- Authorization
- Content-Type
---
apiVersion: "security.istio.io/v1beta1"
kind: "RequestAuthentication"
metadata:
name: "solver-foundation-meta-service"
namespace: "staging"
spec:
selector:
matchLabels:
app: solver-foundation-meta-service
jwtRules:
- issuer: "http://keycloak-http.default/auth/realms/staging"
jwksUri: "http://keycloak-http.default/auth/realms/staging/protocol/openid-connect/certs"
forwardOriginalToken: true
---
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: solver-foundation-meta-service
namespace: "staging"
spec:
selector:
matchLabels:
app: solver-foundation-meta-service
rules:
- from:
- source:
requestPrincipals: ["*"]
The above example depicts employment of Keycloak IDP authentication and authorization, guarding the deployed service.
Monitoring
Introduction of a service that monitors the behavior of all Services, and generate reports on platform behavior. It is based on Prometheus, while cadvisor and node exporter are needed in all database helm charts (containers), and monitoring endpoints in every API service. Embedded Grafana is used to display real-time reports.
Exemplary deployment of Prometheus:
apiVersion: apps/v1
kind: Deployment
metadata:
name: prometheus-deployment
namespace: monitoring
spec:
replicas: 1
selector:
matchLabels:
app: "prometheus-server"
template:
metadata:
labels:
app: prometheus-server
spec:
containers:
- name: prometheus
image: prom/prometheus:v2.2.1
args:
- "--config.file=/etc/prometheus/prometheus.yml"
- "--storage.tsdb.path=/prometheus/"
ports:
- containerPort: 9090
volumeMounts:
- name: prometheus-config-volume
mountPath: /etc/prometheus/
- name: prometheus-storage-volume
mountPath: /prometheus/
volumes:
- name: prometheus-config-volume
configMap:
defaultMode: 420
name: prometheus-server-conf
- name: prometheus-storage-volume
emptyDir: {}
---
apiVersion: v1
kind: Service
metadata:
name: prometheus-service
namespace: monitoring
annotations:
prometheus.io/scrape: 'true'
prometheus.io/port: '9090'
spec:
selector:
app: prometheus-server
type: "LoadBalancer"
ports:
- port: 8080
targetPort: 9090
Exemplary deployment of Grafana:
apiVersion: apps/v1
kind: Deployment
metadata:
name: grafana
namespace: monitoring
spec:
replicas: 1
selector:
matchLabels:
app: grafana
template:
metadata:
name: grafana
labels:
app: grafana
spec:
containers:
- name: grafana
image: grafana/grafana:latest
ports:
- name: grafana
containerPort: 3000
resources:
limits:
memory: "2Gi"
cpu: "1000m"
requests:
memory: "1Gi"
cpu: "500m"
volumeMounts:
- mountPath: /var/lib/grafana
name: grafana-storage
- mountPath: /etc/grafana/provisioning/datasources
name: grafana-datasources
readOnly: false
volumes:
- name: grafana-storage
emptyDir: {}
- name: grafana-datasources
configMap:
defaultMode: 420
name: grafana-datasources
IAM graphical interface example:
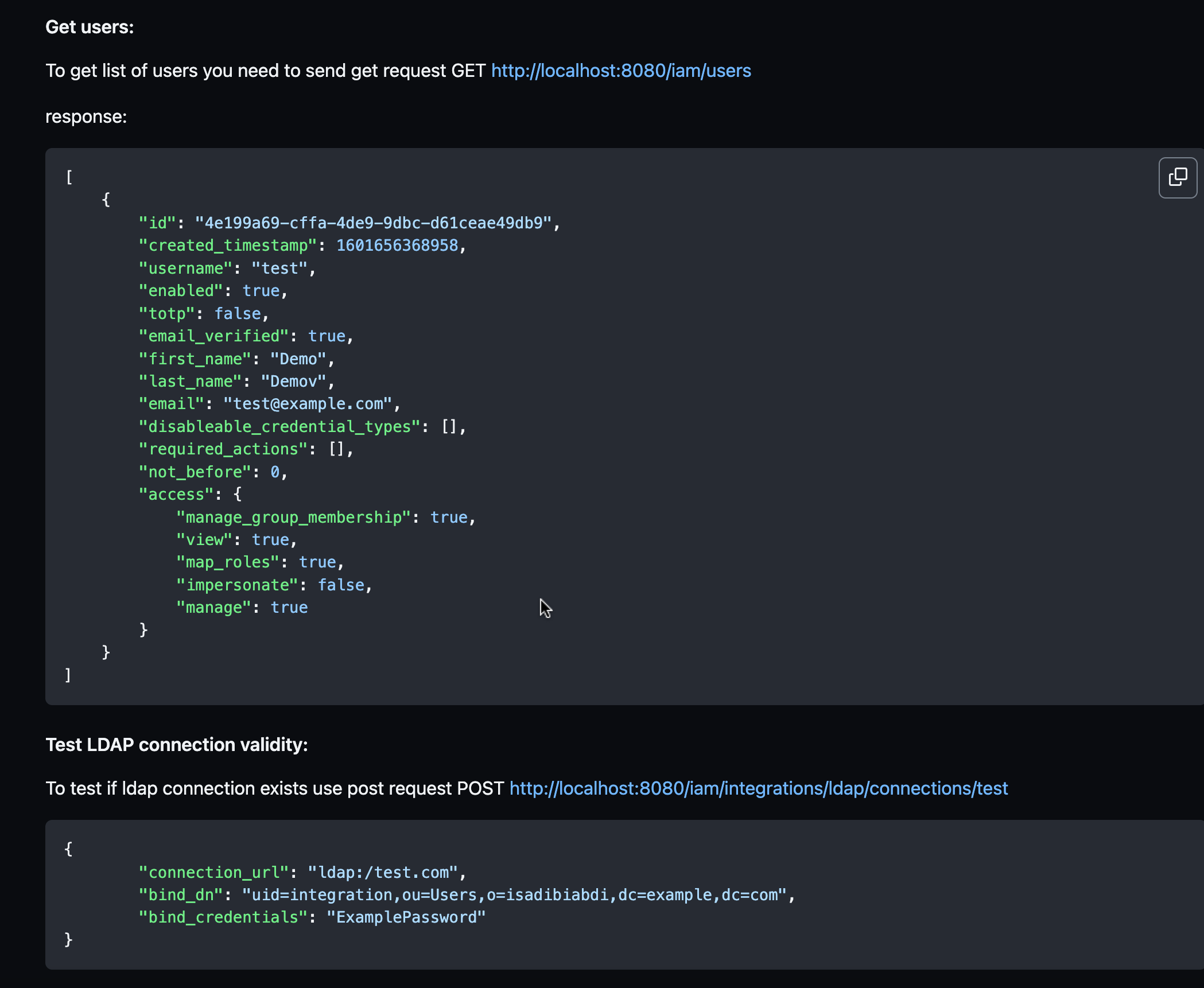
IAM API call examples:
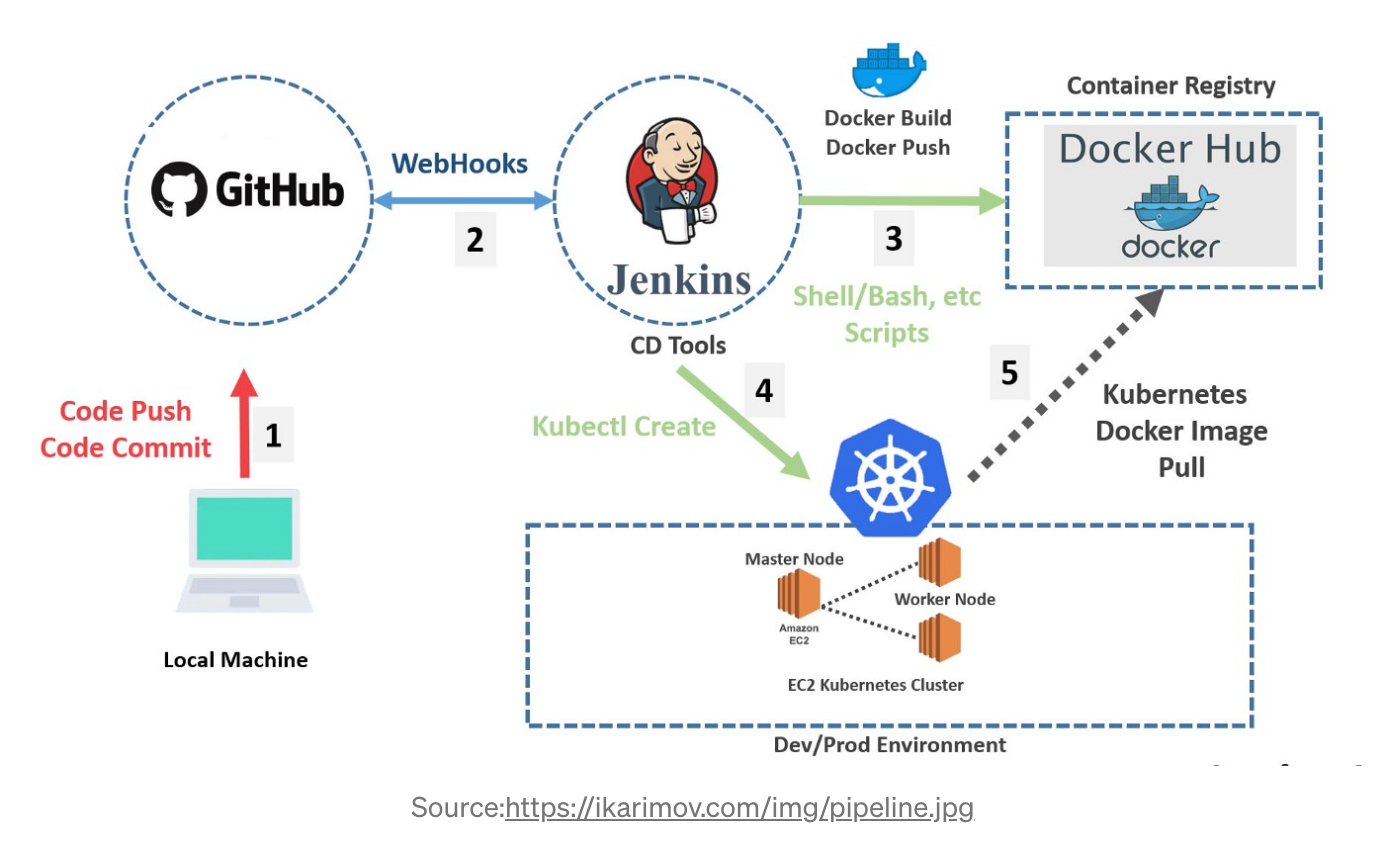
CI/CD on Kubernetes
Continuous Integration diagram
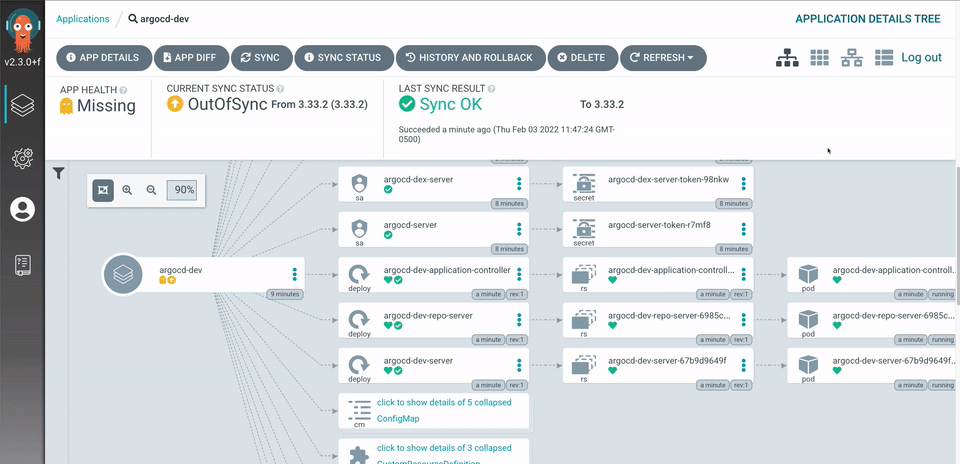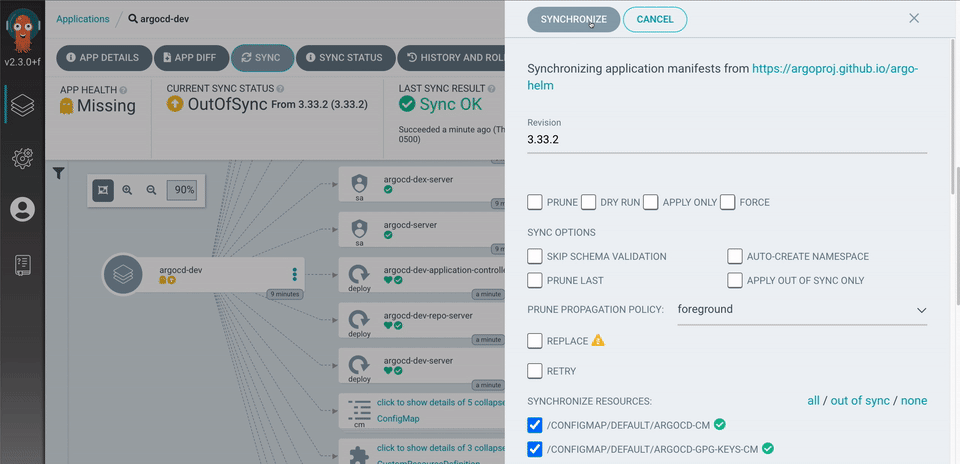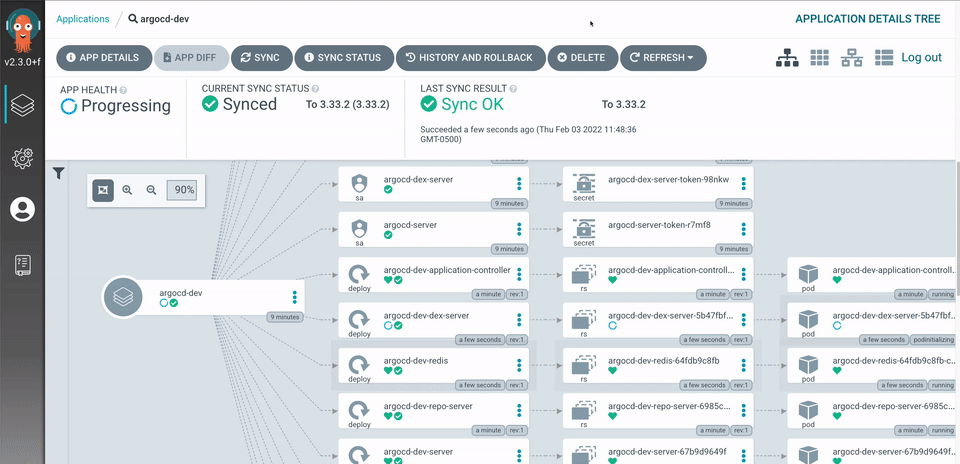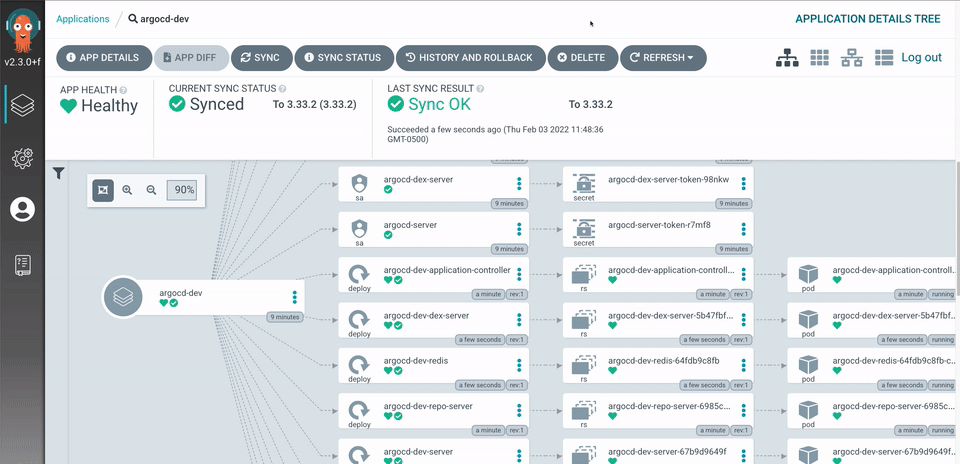
Continuous Deployment via Argo
Why Argo CD?
Application definitions, configurations, and environments should be declarative and version controlled.
Application deployment and lifecycle management should be automated, auditable, and easy to understand.
Argo Workflow Template example
apiVersion: argoproj.io/v1alpha1
kind: WorkflowTemplate
metadata:
name: external-job-template
spec:
templates:
- name: run-external-job
inputs:
parameters:
- name: "job-cmd"
steps:
- - name: trigger-job
template: trigger-job
arguments:
parameters:
- name: "job-cmd"
value: "{{inputs.parameters.job-cmd}}"
- - name: wait-completion
template: wait-completion
arguments:
parameters:
- name: uuid
value: "{{steps.trigger-job.outputs.result}}"
- name: trigger-job
inputs:
parameters:
- name: "job-cmd"
value: "{{inputs.parameters.job-cmd}}"
image: appropriate/curl:latest
command: ["/bin/sh", "-c"]
args: ["{{inputs.parameters.cmd}}"]
- name: wait-completion
inputs:
parameters:
- name: uuid
suspend: {}
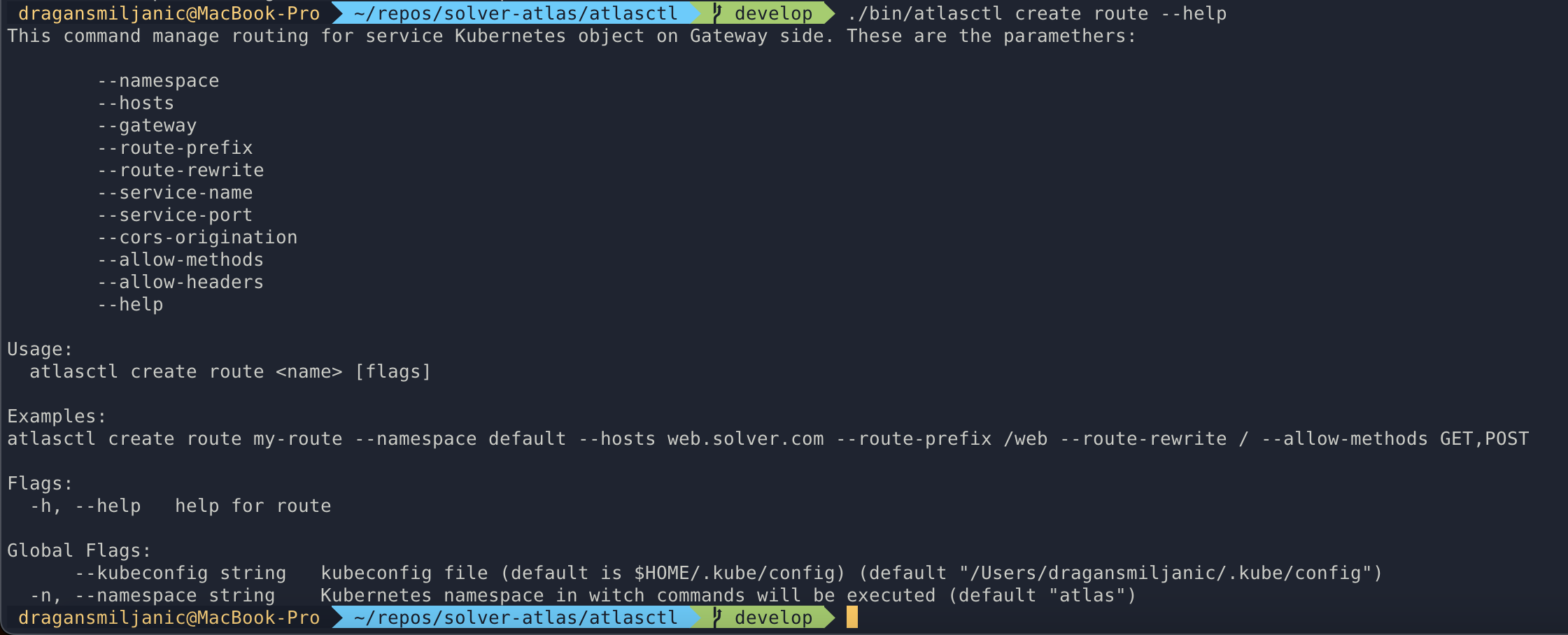
AtlasCTL, powered by Things Solver
Things Solver has begun developing their own command line tool that will facilitate configuration of otherwise scattered Kubernetes cluster resources. The new executable, written in GoLang, aggregates key files that stand essential to building a stable and secure infrastructure inside and upon a K8s cluster, and offers easy use through its user-friendly console interface.
AtlasCTL examples:
Sample use of the command line tool
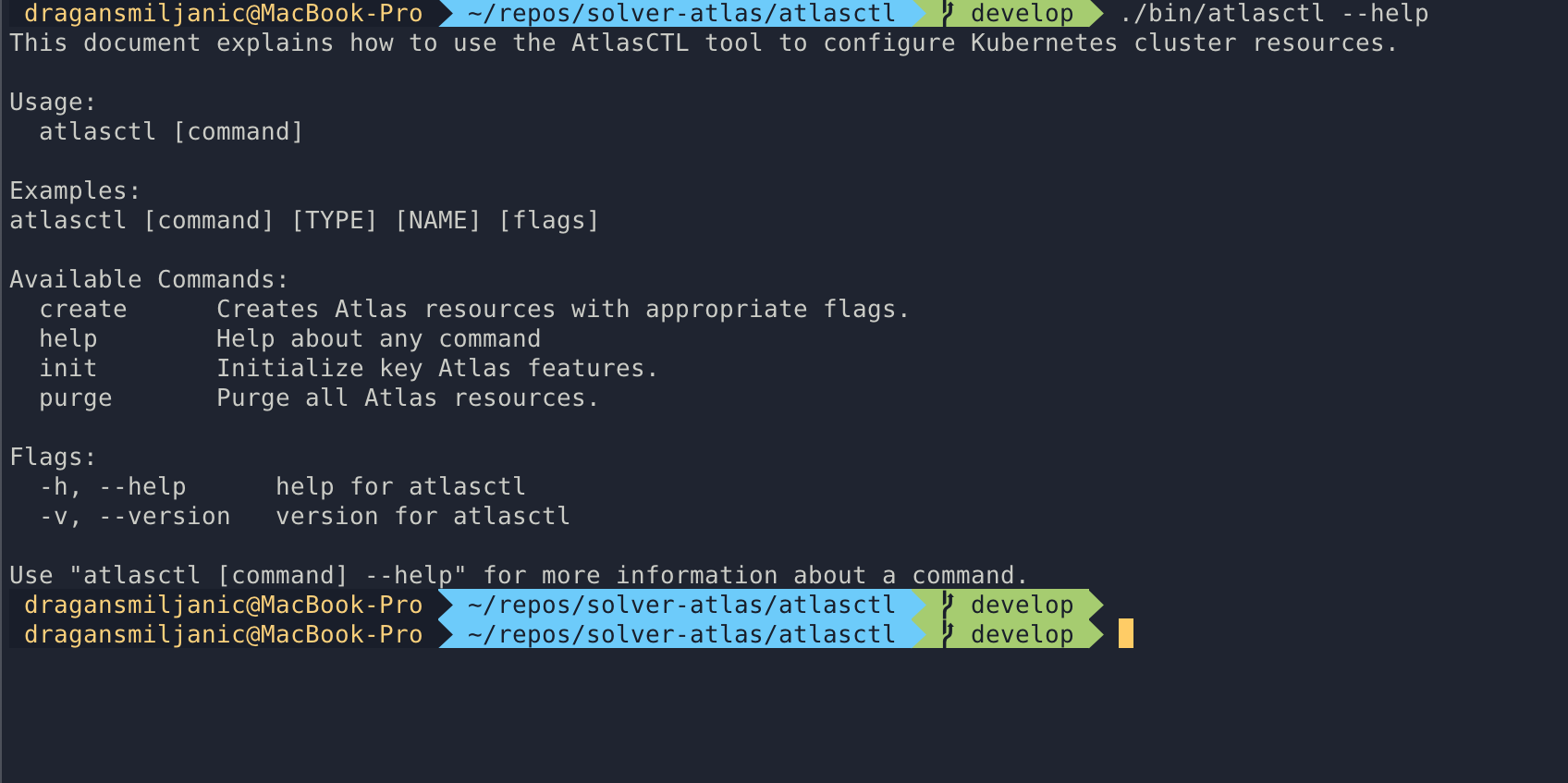
Setting up the backbone infrastructure
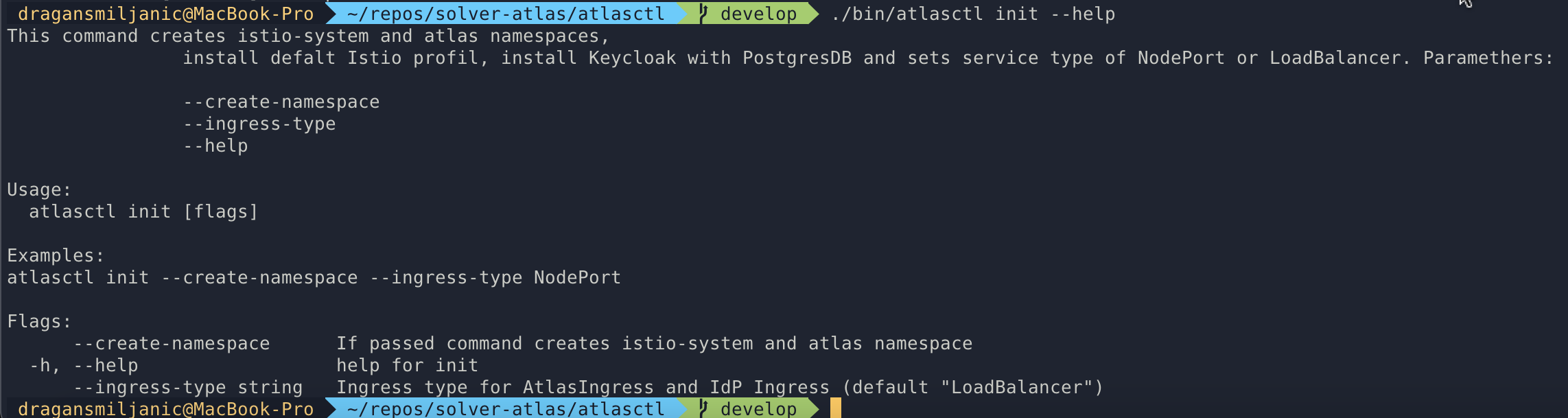
Creation of resources
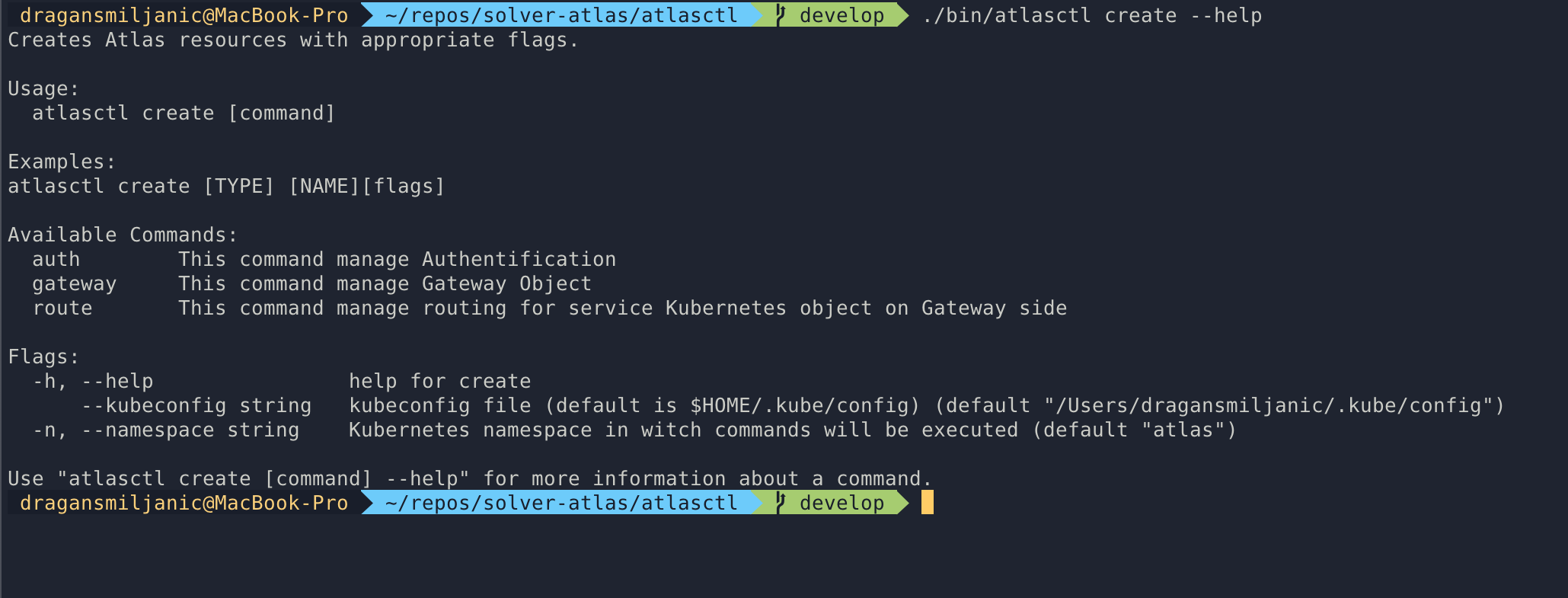
Create gateway
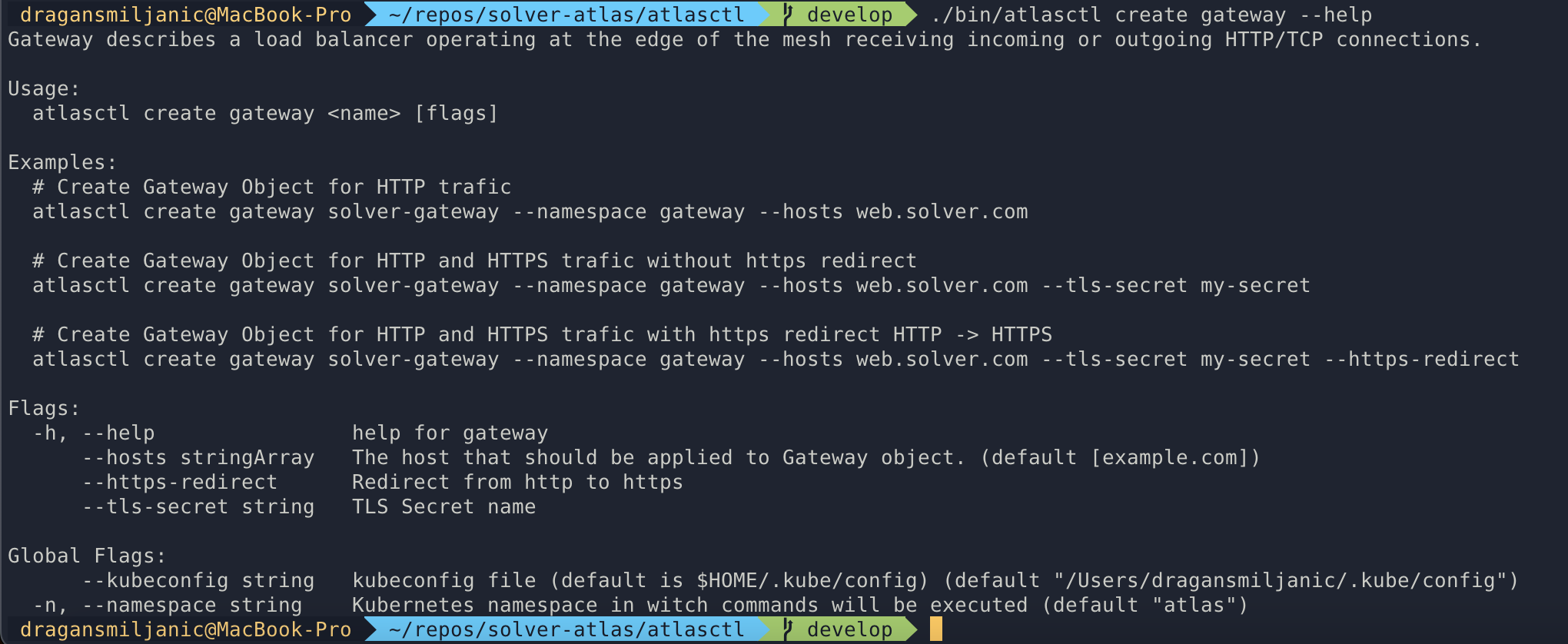
Create route